Introducing tKey: Bringing Two-Factor Authentication and Progressive Security to Private Keys
A New Standard for Non-Custodial Key Management
Today, we’re excited to announce tKey, a modular key management system that allows fully non-custodial (i.e, 2FA) OAuth logins. This provides the security of self-custody with Torus’s ease of use. tKey is going to be available to all Torus customers, and in all Torus products, at no additional cost. Binance Smart Chain is the first developer to integrate tKey.
The first generation of Torus allowed anyone to authenticate with dApps, exchanges or blockchains using only their Google account. Our one-click sign-ins radically lowered the barrier to entry for new users to explore and try decentralized applications. As we continued to build, we added more account authenticators and more tools to help developers make it easier for users to explore their creations.
However, we know that for many crypto users OAuth alone isn’t enough. This is exactly why we built tKey, our version of a completely customizable two-factor authentication (2FA) within Torus.
tKey is a model of threshold key management that solves the security trilemma without sacrificing user experience. It’s flexible and allows end-users to retain autonomy and control. tKey uses Shamir Secret Sharing (SSS) and increases security by leveraging users’ devices, private inputs, and wallet service providers to create multiple layers of progressive security.
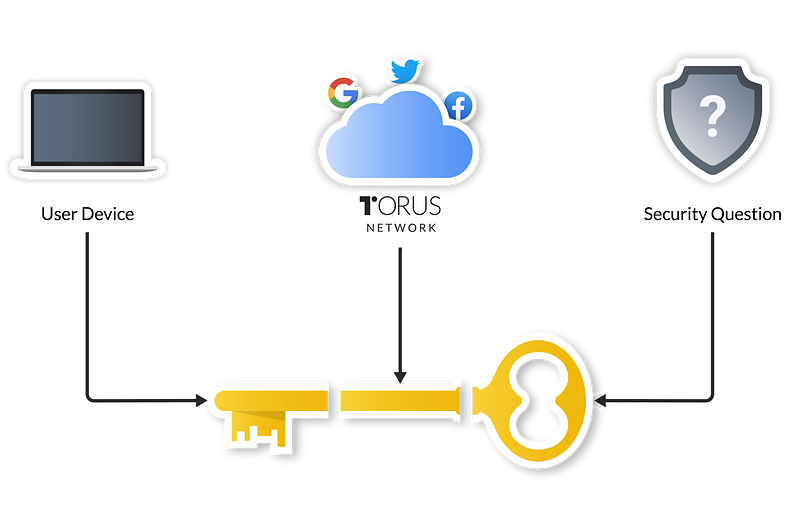
Let’s walk through an example.
Let’s say you create a Torus account by OAuthing into a dApp from your browser. At this point, you’ve created two secret shares: one using your email which is tied to an OAuth token and another which is generated by your wallet service provider via their own authentication flows. In this case, since you’re using Torus, the Torus protocol instructs the Torus Network to conduct a distributed key generation to split and secure your share further, only retrievable via OAuth logins.
If you also have a mobile device, one of your extra security layers could be your phone. It could store your additional secret share in its secure enclave, which is protected by a biometric passcode. If you have more than one mobile device, you could add as many layers of security as you choose. Each implementation of your secret share(s) is device and system specific.
Similar to other 2FA systems, as long as you have access to 2 out of 3 of your secret shares, you will be able to retrieve your private keys and login.
This initial setup provides several benefits for users:
- Convenience — This architecture is compatible with existing user flows, allowing wallet service providers to continue providing a seamless experience for key management.
- Improved to key recovery — In the event of one of your shares getting lost, (e.g. you lose your phone), users can still retain access to their keys, and can revoke access rights from the lost share.
- Non-custodial — Service providers cannot access the user’s private key since they only have one share. They also cannot censor users since the user has a recovery share. Users can also choose to migrate to other service providers.
- Progressive security — tKey gives users more flexibility based on their desired level of security. Increasing the threshold of shares required to reconstruct keys in turn increases the security of their keys (e.g. configuring access to require 3 out of 4 shares).
Just like native private keys, tKeys are off-chain and thus composable with different blockchains and elliptic curves. It naturally is also compatible with on-chain constructions, like multi-sigs and smart contract wallets.
Inline with other threshold cryptography endeavors, tKey is a step towards improving key security for the community as a whole. We’re working hard to also include Threshold Signature Schemes with tKey so that the private key need not be reconstructed in the front-end when signing transactions.
Try Out tKey on Torus
For Decentralized applications on any chain looking to integrate tKey and do so “out of the box” via DirectAuth integrations, head down to Torus to learn more, or reach out to us at hello@tor.us.
Users interested in testing tKey on the Torus Wallet can try it out here.
Users interested in testing tKey on the Torus Chrome Extension (Beta) can install it here.
You can also read more about tKey from the release specification here.





