Interact with Blockchains via AppleID, GitHub, LinkedIn, Twitter, Line and Passwordless Accounts!
Our latest update, v1.7.2, brings 6 new logins to the Torus Wallet and DirectAuth. Users or applications now have the option of creating a new Ethereum blockchain wallet in a single step with any of their following social identities: Google, Facebook, Reddit, Twitch, Discord, AppleID, Github, LinkedIn, Twitter, Line and Passwordless Accounts.

Sending Tokens to Twitter and GitHub Usernames
You can now send tokens to any Twitter and GitHub user, even if that user has never logged into the Torus Wallet before.
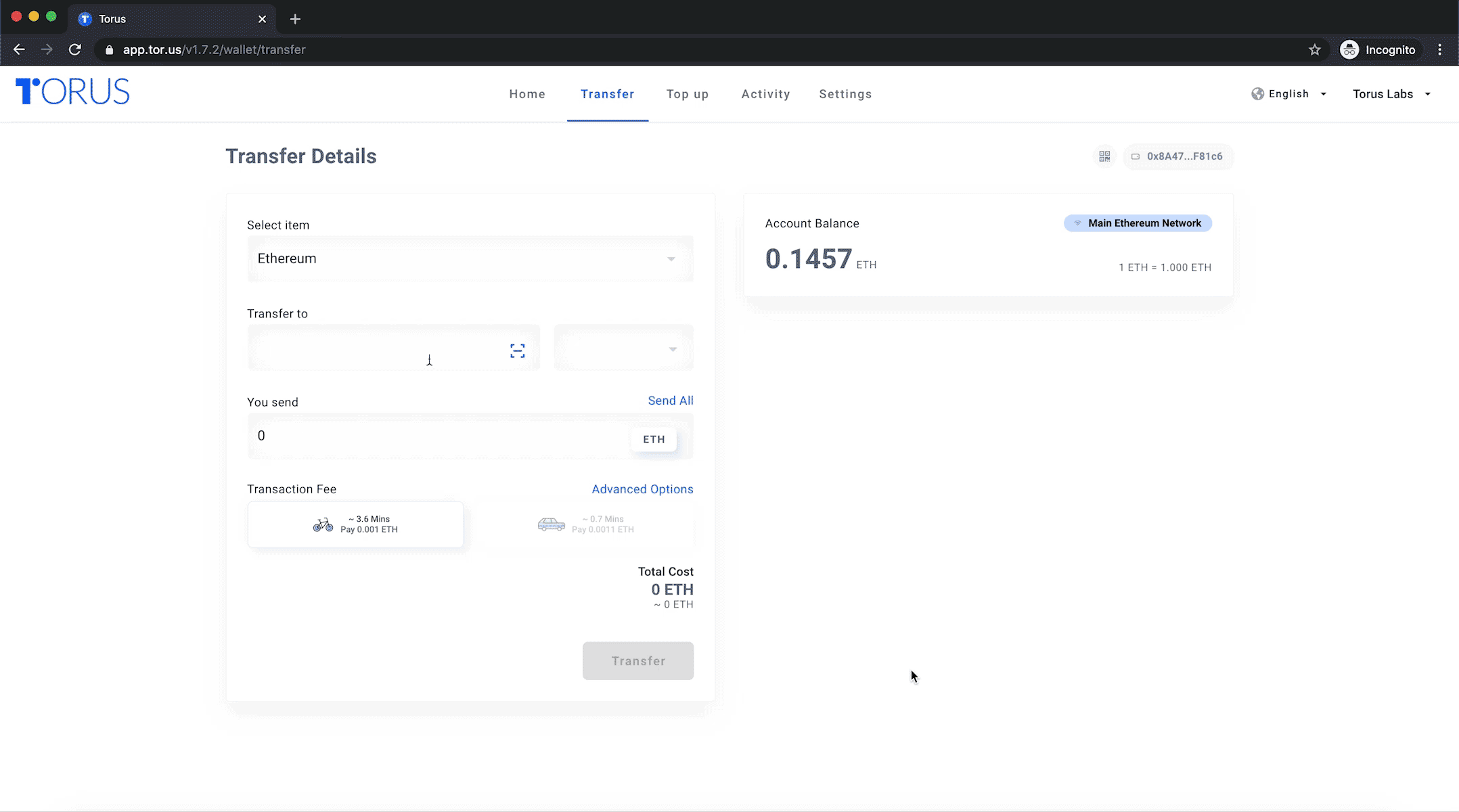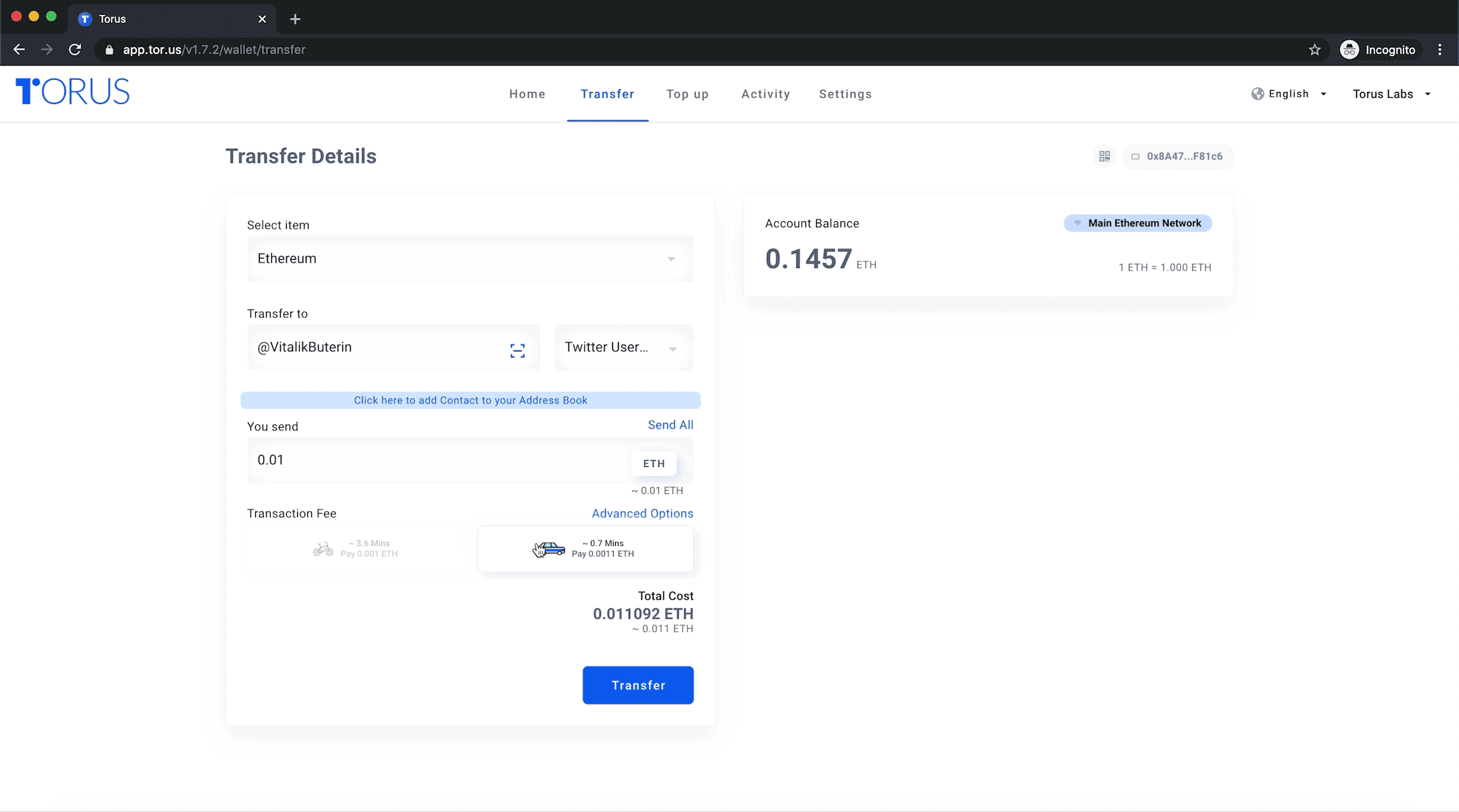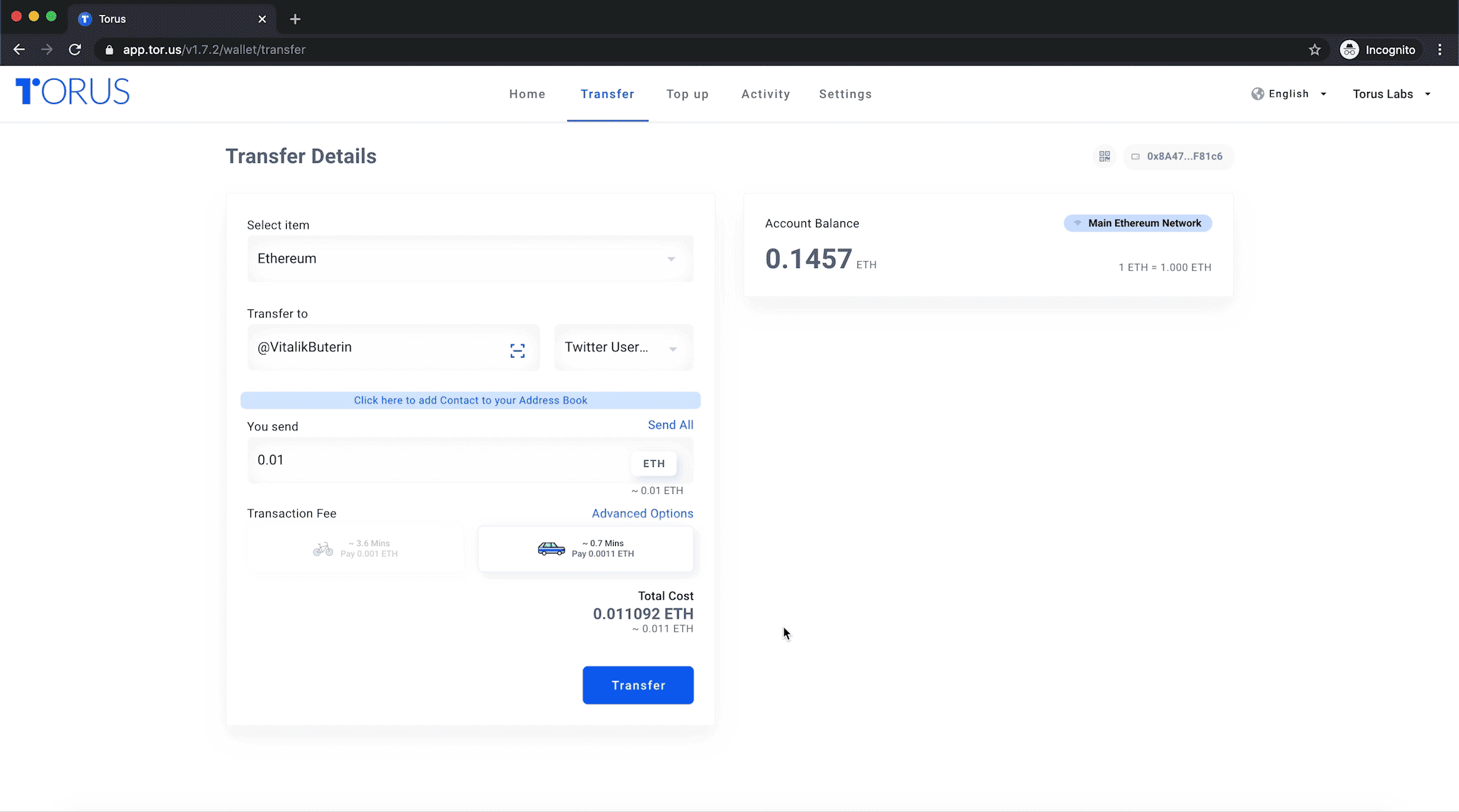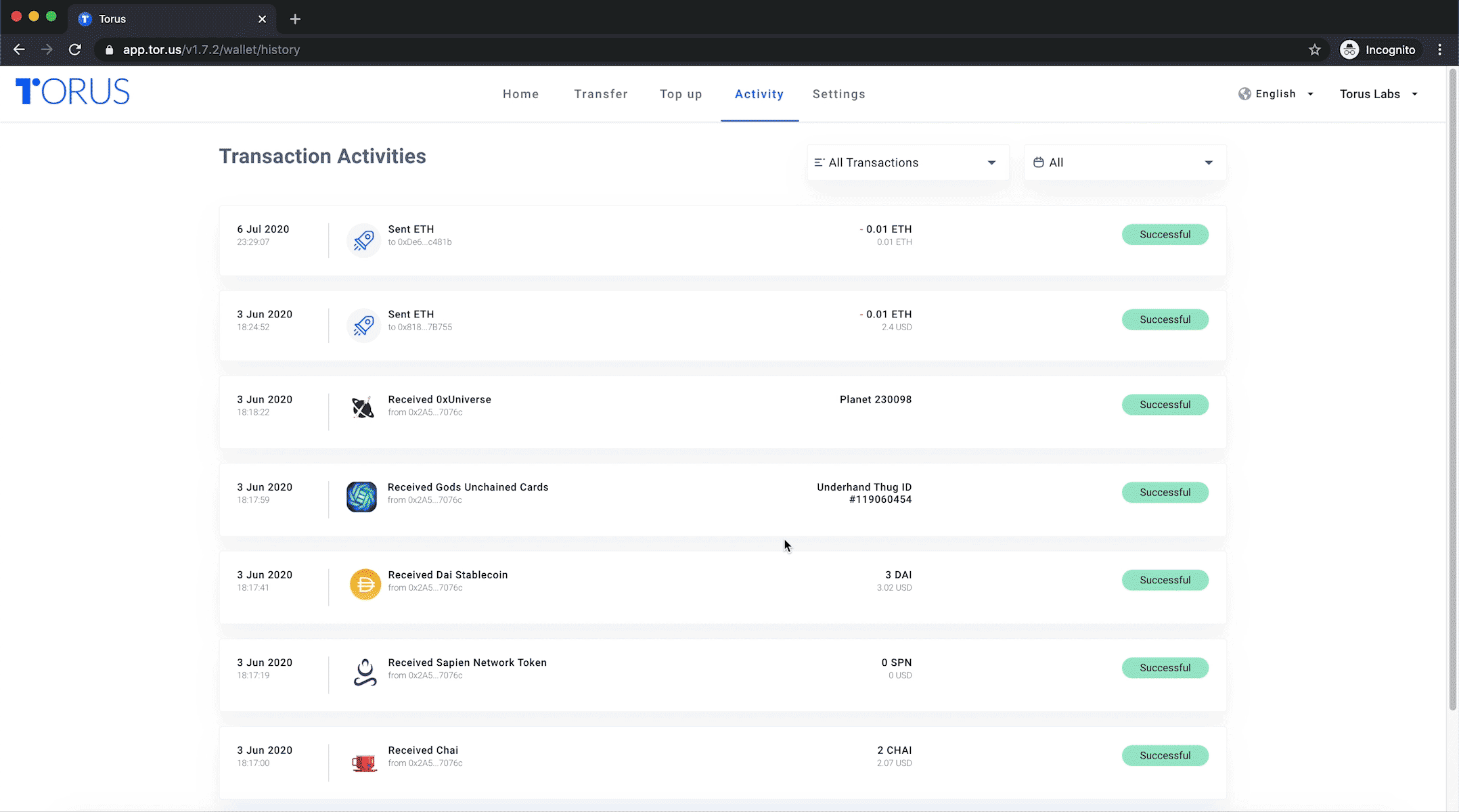
Designed for ease of use and user convenience, these account resolvers are used to enhance the transactions and how users interact with one another on the Torus Wallet and other applications.
Much of the crypto community resides on Twitter, and we are excited to provide the functionality of using those accounts for various use cases. These include simple sends, but also potentially more complex cases such as sybil resistance/quadratic funding.
Some of these have been in the works with projects like Cryptograph, MyCryptoHeroes, Skyweaver and Startrail, which you can look forward to in the near future.
Developers looking to utilize this feature can read more from our documentation.
Trust Assumptions with Proxy Verifiers
Logging into Torus via AppleID, GitHub, LinkedIn, Twitter, Line, or passwordless logins utilizes Auth0, which works as a proxy that links Torus accounts to the verifier (e.g. Twitter or Apple).
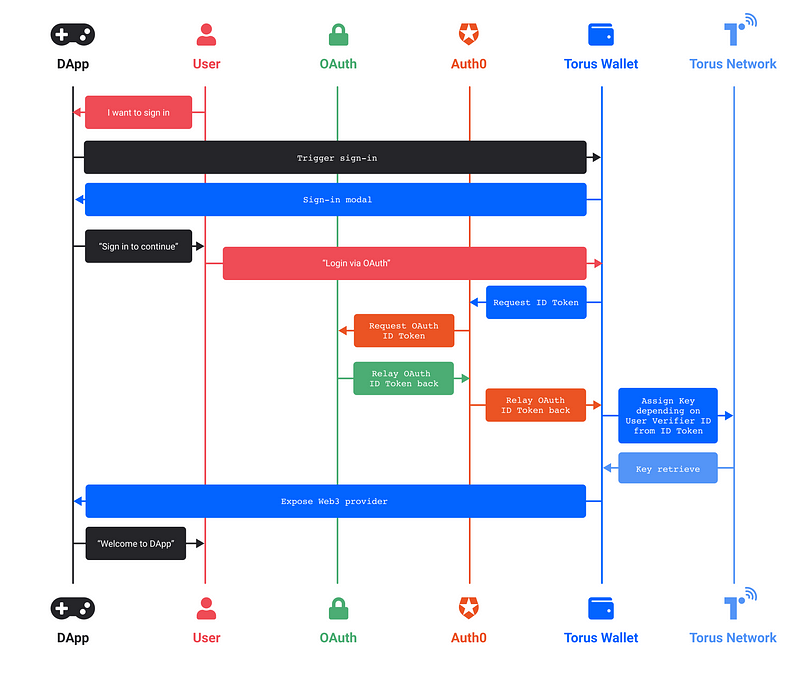
OAuth is a complex standard and is often implemented with different nuances tailored to the provider’s required use cases. For example, both Twitter and GitHub authentication tokens can only be verified once, a condition that is incompatible with the threshold assumptions in the Torus Network. As such, these logins require a proxy to fulfil some of these API requirements.
Users logging into their wallets with our new login methods like Apple and Twitter have a trust assumption with the proxy, Auth0, on top of the original flow. By logging into Torus via these login methods, users are trusting that Auth0 facilitates the login in accordance with the OAuth2.0 standard. This is often done through generic JWT verification methods that are supported by identity solutions like Auth0, Okta, AWS Cognito and others. As the web evolves, solutions like PKCE and other similar tools would allow us to alleviate the need for proxies, and we hope to push these standards forward.
For integrations involving a proxy, we recommend DApps to inform their users that a third-party authenticator is present. Torus has been tailored to easily onboard new users into the decentralised ecosystem, and we recommend incremental layers of security as users get more involved in the ecosystem.
To this end, we’ve been working on a model of device-based key management that essentially allows for self-custodial logins with OAuths. Stay tuned as we’ll be sharing more in the near future!
How Does Torus Work?
To learn more about how Torus works in the backend, you can explore our deep-dive explainers:
What Distributed Key Generation Is
Key Assignments, Resolution and Retrieval
Integrate Torus with your DApp
Keen on offering AppleID, GitHub and Twitter logins to users on your DApp? View our documentation or reach out to us at hello@tor.us to get started on our simple integrations, and expose your DApp to the endless possibilities of mainstream adoption.





