On this page
Multi-Party Computation (MPC) has proven to be one of the most utilized methods for securing crypto wallets. It has supported various functionalities especially in Distributed Key Management, where it practically enabled beginner-friendly ways to access and use keys for crypto wallets. This is why the technology has gained popularity among providers of embedded wallets, Wallet-as-a-Service (WaaS), and crypto platforms—they all use the same MPC mechanism, wherein shares of the key are stored in different locations, and T out of N (T/N) shares are needed to construct a valid signature.
However, the similarities end there. Existing MPC solutions differ by their architecture, level of security, as well as the complexity of computation needed to reconstruct the keys or create a signature with the shares. In this comprehensive analysis, we delve into the four main categories of MPC-based key management systems, dissecting their properties, strengths, and limitations:
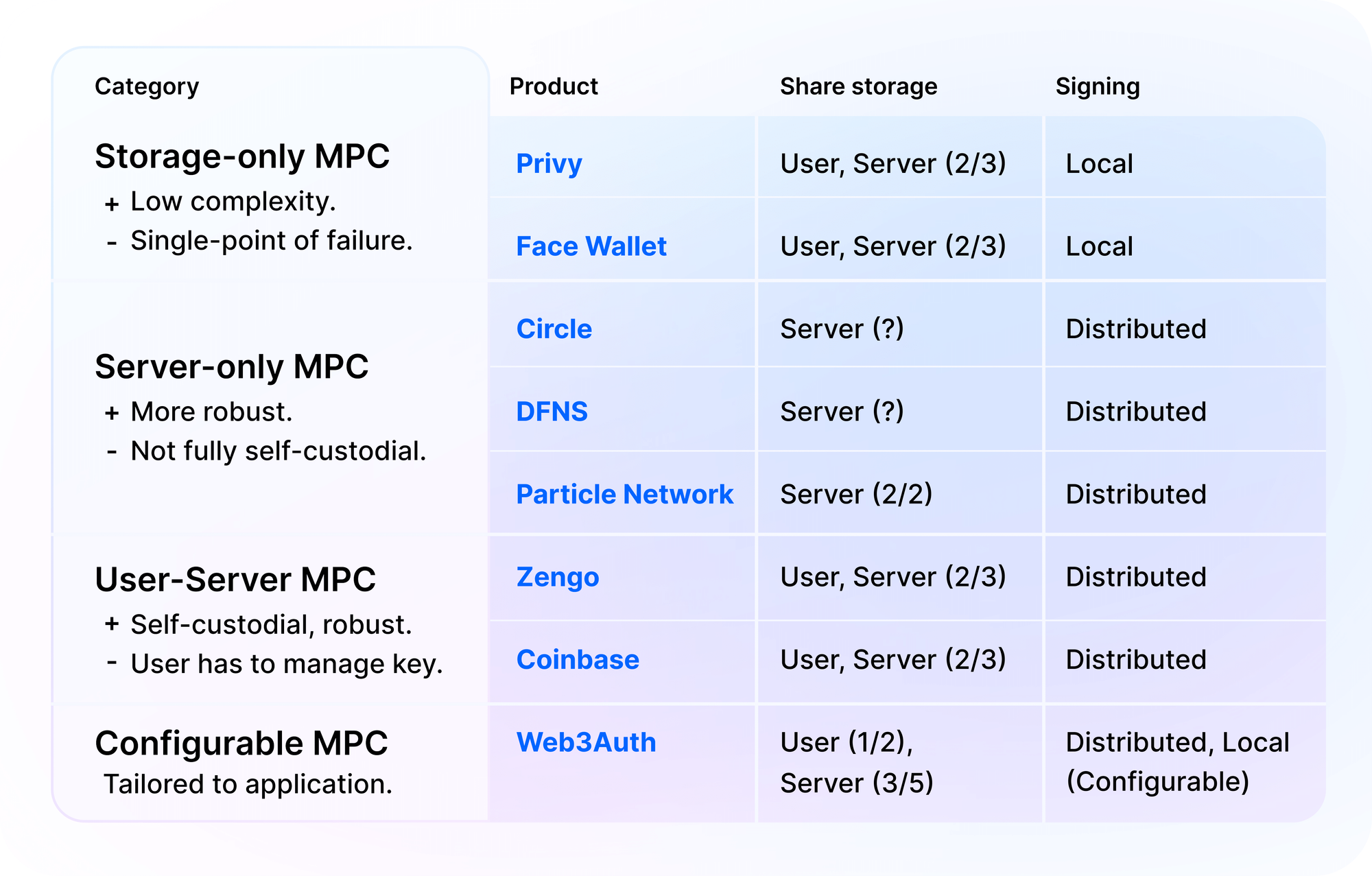
1. Storage-only “MPC”
Who Uses It: Privy, Face Wallet
The first category includes systems that use MPC technology exclusively for storing cryptographic keys, without involving MPC in the signing process. In essence, while the key storage mechanism employs MPC techniques, the actual signing of transactions occurs on the user's device without engaging in any multiparty computation.
Advantage: Ease of Implementation
By sidestepping the complexities associated with MPC-based signing protocols, storage-only MPC offers a straightforward approach to key management with minimal computational effort.
Disadvantage: Single Point of Failure
However, this simplicity comes at a cost. Since the key is reconstructed on the user's device during the signing process, it introduces a single point of failure. Malware or compromised devices could potentially lead to the theft of the reconstructed key, undermining the entire system's security.
Debatably, the designation of these systems as "MPC" is somewhat contentious since they do not entail genuine multi-party computation. Instead, they merely utilize MPC techniques for secure key storage, while the signing process remains localized to the user's device.
2. Server-only MPC
Who Uses It: DFNS, Particle Network, Circle
Moving to the second category, we encounter systems that store all key shares on servers and execute distributed protocols exclusively for generating signatures. In contrast to storage-only "MPC," the signing process here involves genuine multi-party computation among the servers, ensuring the private key is never fully reconstructed at a single location.
Advantage: Robustness
Server-only MPC systems offer enhanced resilience against single points of failure compared to their storage-only counterparts. Since the private key is never reconstructed on any single device, the risk of key exposure due to device compromise is mitigated.
Disadvantage: Limited Self-Custody
Despite the distributed nature of the signing process, these systems do not afford full self-custody to users. With all key shares stored on servers, users relinquish direct control over their cryptographic keys, placing trust in the server infrastructure to safeguard their assets.
Additionally, implementing distributed signing protocols introduces complexity, both in terms of system architecture and protocol design, potentially impacting performance and usability.
3. User-server MPC
Who Uses It: Zengo, Coinbase
The third category encompasses systems that distribute key shares between users and servers, facilitating distributed signing protocols that require cooperation between the two parties. In these systems, the user retains partial control over key material, participating in the signing process while leveraging server-side resources.
Advantage: Partial Self-Custody
User-server MPC systems balance decentralization and usability by involving users in the signing process. While key shares are distributed between users and servers, users control a piece of the key that is necessary to generate signatures, ensuring a great degree of self-custody over their assets.
Disadvantage: Complexity
The involvement of both users and servers in the signing process introduces complexity and overhead. Users must manage key share material, necessitating careful handling to prevent key leakage over time. Additionally, implementing distributed signing protocols adds computational overhead and may require specialized client-side software.
4. Configurable MPC
Who Uses It: Web3Auth
The fourth and most versatile category comprises systems that offer configurable MPC platforms, allowing users to tailor their key management setup to suit their specific requirements. These systems provide flexibility in choosing key storage mechanisms, signing protocols, and the distribution of key shares, empowering users to customize their security model.
Advantage: Customizability
Configurable MPC platforms offer unparalleled customization, enabling users to fine-tune their key management setup to align with their security preferences and use-case requirements. From choosing between storage-only or user-server setups to configuring the distribution of key shares, users have full control over their security model.
Disadvantage: Complexity
While configurable MPC platforms provide flexibility, they also require an understanding of best practices to create a good balance of security, simplicity, and usability. For example, an extremely decentralized configuration may introduce additional complexity in protocol design and implementation, potentially impacting performance and user experience.
But worry not. If you are using Web3Auth’s configurable MPC, the community and the team is always here to help you decide the best way to customize the solution for your application’s needs.
Conclusion: Not all MPC solutions are made equal
MPC-based key management systems encompass a diverse array of approaches, each with its unique properties, strengths, and limitations. From storage-only solutions offering simplicity at the expense of self-custody to configurable platforms offering the highest degree of control, users must carefully evaluate their options to select the system that best aligns with their security requirements and operational needs.
As the decentralized ecosystem evolves, the importance of robust and flexible key management solutions cannot be overstated. By understanding the distinctions between different categories of MPC-based key management systems, users can make informed decisions to safeguard their assets and preserve their autonomy in the digital realm.
If you are interested to try an MPC SDK that works for everyone, check out Web3Auth’s configurable MPC!